29593
SEEKS AND IDENTIFIES
ANTIC QUANTUM ENCRYPTION
USA, New York
Market: Financial services, Gadgets, Blockchain, Crypto currency
Stage of the project: Prototype or product is ready
Date of last change: 18.06.2018
USA, New York
Market: Financial services, Gadgets, Blockchain, Crypto currency
Stage of the project: Prototype or product is ready
Date of last change: 18.06.2018
Idea
Multilevel multifactor authenticator with elementary storage. Multi-level protection with an increase in the number of levels without changing the product.
Current Status
MVP (minimum viable product)
Market
1. Large-scale interbank operations. 2. Work by the subject of banking operations. 3. Authentication of ownership of the object. 4. Hidden protection of property rights to the object and files on the Internet. 5. Reliable database protection.
6. Reliable protection of offline devices from hacking. 7. Registration on the portal in the Internet. 8. Blocking of unauthorized use of content on the Internet.
Problem or Opportunity
1. Provides multi-level protection with an increase in the number of levels without changing the product. 2. Guarantees recovery with loss of passwords at any number of security levels. 3. File transfer does not require a special transfer system and can use the already created ones. 4. You can use multi-channel transmission with the base distribution. 5. It is possible to transfer data in the stream, including the video stream. 6. Allows you to secretly encode content from unauthorized use. 7. Block unauthorized use of content on the Internet. 8. GUARANTEED PROTECTION AGAINST USE OF QUANTUM COMPUTERS.
Solution (product or service)
http://www.defin.hol.es/
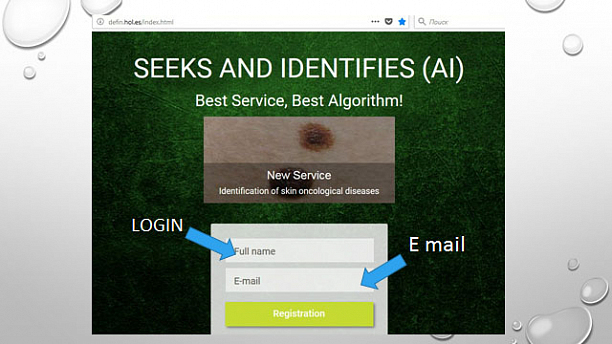
1. Through the window "Search for images" we get to the registration page.
2. We pass registration: we fill our E - mail - and login and go to the work page "Upload image".
3. Through the "Upload Image" window we load our image for a special codification.
4. Your already encoded image will come to your mail.
5. Downloading the sent image to the service gives you access to it.
1. Through the window "Search for images" we get to the registration page.
2. We pass registration: we fill our E - mail - and login and go to the work page "Upload image".
3. Through the "Upload Image" window we load our image for a special codification.
4. Your already encoded image will come to your mail.
5. Downloading the sent image to the service gives you access to it.
Competitors
QR, quantum encryption, emoji
Advantages or differentiators
1.The level of authentication protection is higher than the two-factor authentication level. 2. Authentication does not require a mobile network.
3. Not tied to the device ID. 4. No need for SMS messages. 5. Allows easy recovery of lost passwords. 6. The time of breaking approaches infinity.
7. Hacking is fixed when trying to break into lower levels. 8. The volume of the encoded content is unlimited, unlike the QR code. 9. Hidden encoding of the information flow. 10. Is able to provide content from hacking with the help of quantum computers.
3. Not tied to the device ID. 4. No need for SMS messages. 5. Allows easy recovery of lost passwords. 6. The time of breaking approaches infinity.
7. Hacking is fixed when trying to break into lower levels. 8. The volume of the encoded content is unlimited, unlike the QR code. 9. Hidden encoding of the information flow. 10. Is able to provide content from hacking with the help of quantum computers.
Finance
100000$
Business model
Business model
1. B2B
2. B2C
3. SaaS
1. B2B
2. B2C
3. SaaS
Money will be spent on
On marketing, advertising and attracting customers
Offer for investor
25% of the share capital for 100000 $
Team or Management
Risks
Seed round
Incubation/Acceleration programs accomplishment
MHP accelerate program
Won the competition and other awards
11 patents, MHP final
Invention/Patent
1. А. с. 215915 СССР, пріоритет від 3.05.1984 р.,
2. А.с. 242003 СССР, пріоритет від 10.06.1985 р.,
3. А.с. 243524 СССР, пріоритет від 01.07.1985 р.,
4. а.с. 249773 СССР, пріоритет від 20.03.1985 р.,
5. а.с. 260114 СССР, пріоритет від 1.09.1987 р.,
6. а.с. 1186389 СССР,
7. а.с. 1121096 СССР,
8. а.с. 1294476 СССР,
9. а.с. 1279748 СССР,
10. Патент України 106047 заяв. 09.11.2015, опубл. 11.04.2016.
10. Патент України 116470, заяв. 09.11.2015, опубл. 11.04.2016.
2. А.с. 242003 СССР, пріоритет від 10.06.1985 р.,
3. А.с. 243524 СССР, пріоритет від 01.07.1985 р.,
4. а.с. 249773 СССР, пріоритет від 20.03.1985 р.,
5. а.с. 260114 СССР, пріоритет від 1.09.1987 р.,
6. а.с. 1186389 СССР,
7. а.с. 1121096 СССР,
8. а.с. 1294476 СССР,
9. а.с. 1279748 СССР,
10. Патент України 106047 заяв. 09.11.2015, опубл. 11.04.2016.
10. Патент України 116470, заяв. 09.11.2015, опубл. 11.04.2016.
Photos
Presentation
Sign in/Sign up